Artificial intelligence (IA) quickly went from buzz to trade need in the past year – something that Zscal has seen the Pioneer of IA -powered solutions and following the activity of AI / ML companies in the largest safety cloud in the world. Companies are increasingly adopting AI tools to improve productivity, automate workflows and speed up decision -making. However, cybercriminals take advantage of the same technology to scale sophisticated attacks, hyper-realistic depths to advanced phishing patterns.
With the AI fundamentally changing both the operation of companies and how cybercriminals attack, organizations must maintain a current and complete understanding of the company’s AI landscape. The star Threatlabz 2025 IA security report Examine the intersection of business use and security, drawing information from 536.5 billion AI / ML transactions in the zero zero trust.
The report reveals how companies around the world and between industries use and manage IA / ML tools, highlighting their advantages and security problems. It examines the increase in risks associated with AI, cybercriminals arming AI to the implications of security for recent IA progress as Deepseek, while offering best practices to mitigate these risks.
5 key conclusions: Trends of use and threats of AI
The Threatlabz research team analyzed the activity of more than 800 known AI / ML requests between February and December 2024. Here are the notable results:
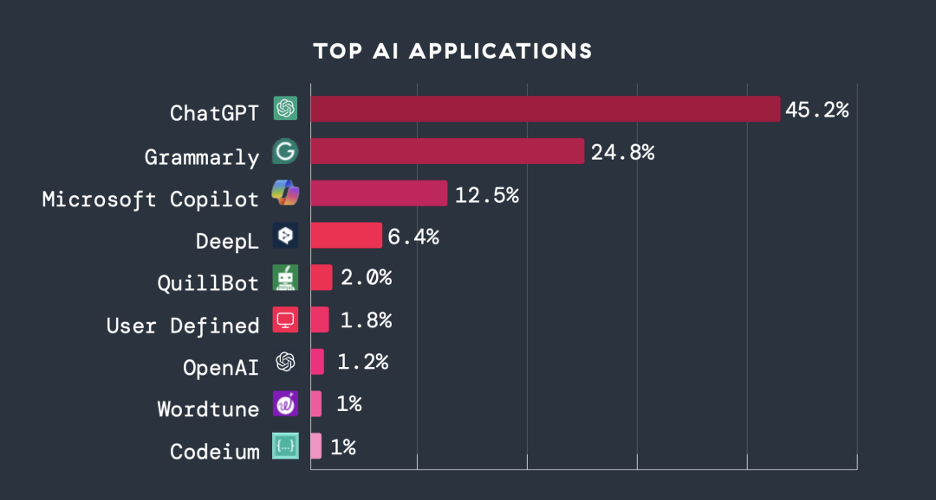
1. USE AI / ML has increased exponentially: AI / ML transactions in the ZSCALALL cloud increased by 36x (+ 3,464.6%) from year to year, highlighting the explosive growth in the company’s adoption. The rise in power was fueled by Chatgpt, Microsoft Copilot, Grammarly and other generative AI tools, which represented the majority of AI traffic from known applications.

Zscater
Figure 1: Upper IA applications by transaction volume
2. Companies have blocked a large part of AI transactions: 59.9% of AI / ML transactions were blocked, signaling concerns about data security and uncontrolled use of AI applications. While organizations are working to establish IA governance executives, many adopt a cautious approach, restricting access to certain AI applications when they refine policies around data protection.
3. The United States and India stimulate IA / ML traffic The most: The United States and India has recorded the highest volume of AI / ML transactions in the Zscal Cloud, reflecting a strong business adoption and an increasing concentration of IA-focused innovation. The other main contributors include the United Kingdom, Germany and Japan, each presenting different levels of AI / ML activity.
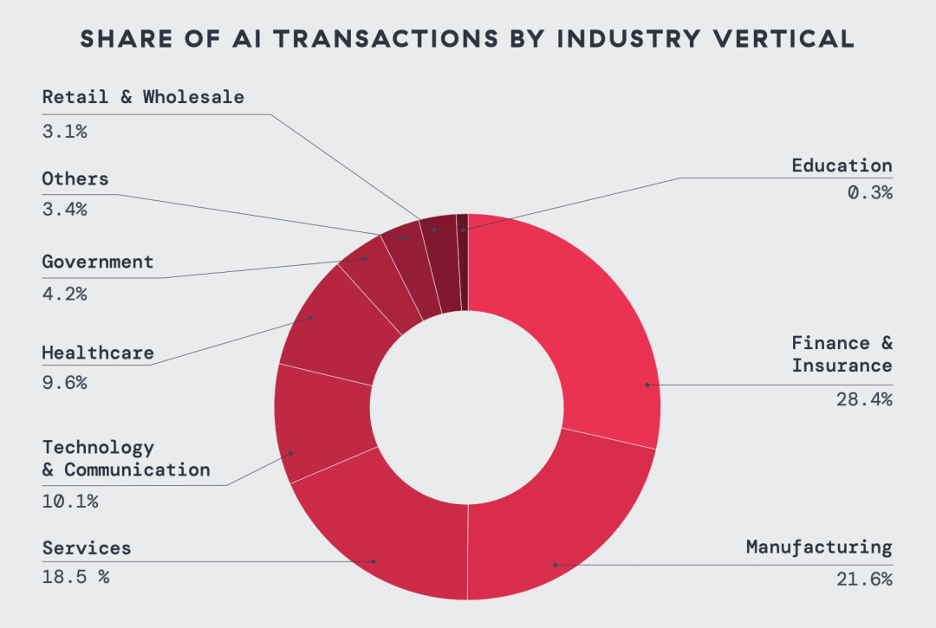
4. Finance and insurance and manufacturing dominate the adoption of AI: The finance and insurance sectors (28.4%) and manufacturing (21.6%) generated the most of IA / ml traffic. Following them, technology, health care and government integrate AI at variable rates when sailing in driving between adoption and apprehension.

Zscater
Figure 2: Industries leading the largest proportions of AI transactions
5. The cyber liking led by AI increase: Threat actors take advantage of AI to improve phishing campaigns, automated attacks and create realistic content Deepfake. Threatlabz researchers have shown how Deepseek can be manipulated to quickly generate phishing pages that imitate trusted brands. In addition, Threatlabz discovered a campaign of malicious software in which the attackers created a false AI platform to exploit the interest of AI and to deceive the victims to download malicious software.
Secure AI and extinguish threats from AI with Zscaler
THE Threatlabz 2025 IA security report Provides detailed advice for companies that seek to adopt AI safely while minimizing risks and stopping cyber-starts fueled by AI.
Companies must rethink security strategies to take into account new vulnerabilities, expanded attack areas and Cyberattacks powered by AI. Traditional security approaches depending on firewalls and VPNs are terribly insufficient against speed and sophistication of threats fueled by AI. Companies must adopt a zero confidence approach, eliminate implicit confidence, apply the least privileged access and constantly check all AI interactions.
Zscater Zero trust architecture Give Zero Trust everywhere – securing the user, workload and IoT / OT communications – Infused with Complete AI capabilities. Its AI models detect and disrupt advanced threats, blocking millions of attacks per day to improve business security results and mitigate emerging risks.
The report details how to stop the threats fueled by AI with Zscaler, in particular:
- Zero trust architecture: Reduce the attack surface by hiding applications and IP addresses from attackers and applying the least privilege access.
- Cyber-stage protection fueled by AI: Detect and block phishing campaigns generated by AI, contradictory exploits and malware led by AI in real time.
- Classification of data fed by AI and DLP: Use the IA -led classification to detect and protect sensitive data on the Zscal data fabric.
- Segmentation of applications powered by AI: Stop the lateral movement in the networks, ensuring that attackers cannot easily degenerate privileges or access critical systems.
- Violation prediction fed by AI: Pre -emptional potential violation scenarios using generative predictive models and multidimensional predictive models.
- IA badges in real time: Use a predictive and generative AI for usable information that improves safety operations and digital performance.
- Visibility of AI: Get in -depth visibility in trends and interactions of the AI application via interactive dashboards.
Get the report
Download the AI Threatlabz 2025 security report For additional data -based information and IA impact analysis on cybersecurity, with expert advice to help companies adopt AI and mitigate its risks.


